Many startups migrating to the cloud may want to keep some of their data in an on-premise server. Accessing the data from the cloud is then tough, because most likely the data should not go over the public internet for security reasons. AWS offers Direct Connect as an enterprise solution for dedicated hybrid traffic. But Direct Connect’s high cost and long installation time is too much for many startups. Given time and money constraints, AWS Site-to-Site Virtual Private Network (Site-to-Site VPN) is a better solution. I followed Chetan Agrawal’s demo and enhanced it with a few bells and whistles to investigate the workings of a VPN.
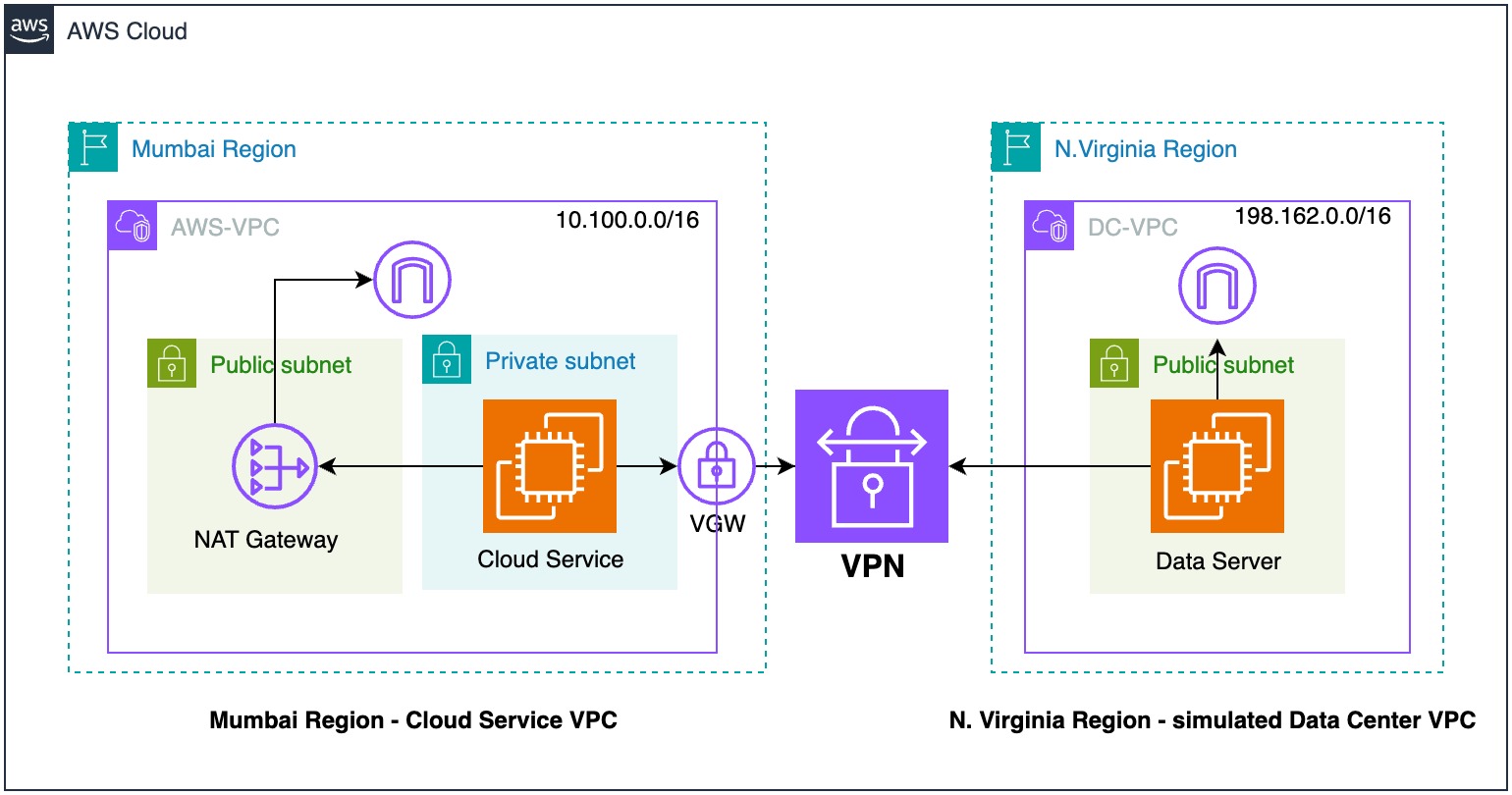
To simulate a cloud service and an on-premises Data Center, there are two VPC’s in separate regions: us-east-1 (N. Virginia) and ap-south-1 (Mumbai). The Mumbai VPC (“AWS-VPC”) represents a AWS service running in the cloud. It consists a 2023 Linux server in in a private subnet. The server’s user data script (below) install and starts an http server, htttpd. The script then queries it’s own metadata endpoint (169.254.169.254) to find it’s own private IP. and creates a static web page (index.html) which prints out the instance’s private IP.
#!/bin/bash sudo su yum update -y yum install -y httpd systemctl start httpd systemctl enable httpd TOKEN=curl -X PUT "http://169.254.169.254/latest/api/token" -H "X-aws-ec2-metadata-token-ttl-seconds: 21600" IP=$(curl -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data/local-ipv4) echo "Coming to you live from local ip: $IP" > /var/www/html/index.html
Because the yum installer must reach out to the public internet to install the httpd server, there is a public subnet in the AWS-VPC with a NAT (“Network Address Translation”) Gateway. Web-bound traffic (0.0.0.0/0 ip range) is led to the NAT Gateway by an entry in the private subnet’s route table. Secondly there is a Virtual Private Gateway (VPG) in the private subnet which forms one endpoint of the VPN tunnel. In the private subnet route table all traffic destined for the Data Center (ip range 192.168.0.0/16) is routed to the VPG.

On the other side of the connection, the N. Virginia Data Center VPC, there is a Linux server in a public subnet. This server represents the static endpoint (“Customer Gateway”) of the Site-to-Site VPN. The VPN tunnel can then be launched, joining the Virginia “AWS Cloud” VPC to the Mumbai “Data Center” VPC.
To set a the VPN tunnel, I installed and ran the VPN software (openswan) on Data Center instance. Configuration instructions can be downloaded from the VPG listing in the AWS console. I waited for the VPN tunnel to turn green in the console. An encrypted (ipsec – IP with security) tunnel was now in place between the Mumbai and N. Virginia VPCs.
Then the moment of truth – time to test the connection. I sshed into the N. Virginia Data Center instance (192.168.0.105 local IP) and pinged the private ip of Mumbai AWS-VPC private instance (10.100.0.74). Unfortunately the ping went unanswered.

To investigate I checked the two instances’ security group settings. The tcp and icmp security rules were correct for ping and http traffic. The AWS Reachability Analyzer wasn’t helpful in this case, maybe because it did not play nice with the VPN software.
Then I discovered that the route table of the AWS-VPC cloud private subnet had an improper configuration. Instead of targeting the correct IP range of the Data Center cloud (192.168.0.0/16) to the Virtual Private Gateway, I erroneously typed something like 162.168.0.0/16. Upon correcting the route table entry – voila – traffic started flowing. I could now ping and curl the private ip of the Mumbai AWS-VPC server from the N. Virginia Data Center-VPC instance.

curling the private ip of the Mumbai server (10.100.0.74) returned the html confirmation message.
Coming to you live from local ip: 10.100.0.74
🏕️ I was a happy camper. But, debugging entailed a few hours of frustration caused by a single typo. Human Error was the culprit. In the future I hope to configure a Site-to-Site VPN with an AWS Cloud Development Kit (cdk) script.



0 Comments